
Multi factor authentication at best price in Bengaluru by Integra Micro Systems Private Limited | ID: 21403645130

Alex Xu on X: "Top 4 Forms of Authentication Mechanisms 1. SSH Keys: Cryptographic keys are used to access remote systems and servers securely 2. OAuth Tokens: Tokens that provide limited access
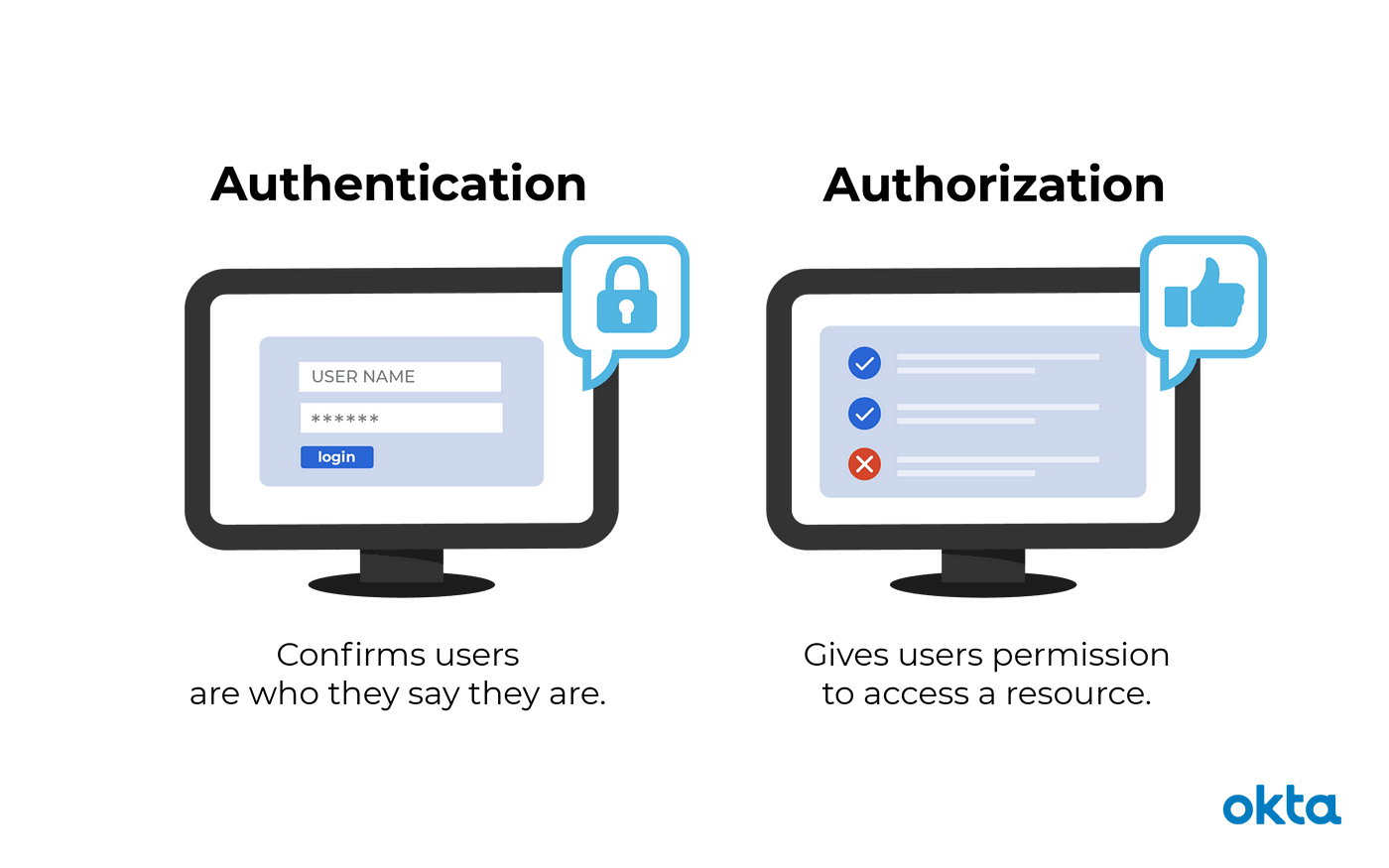
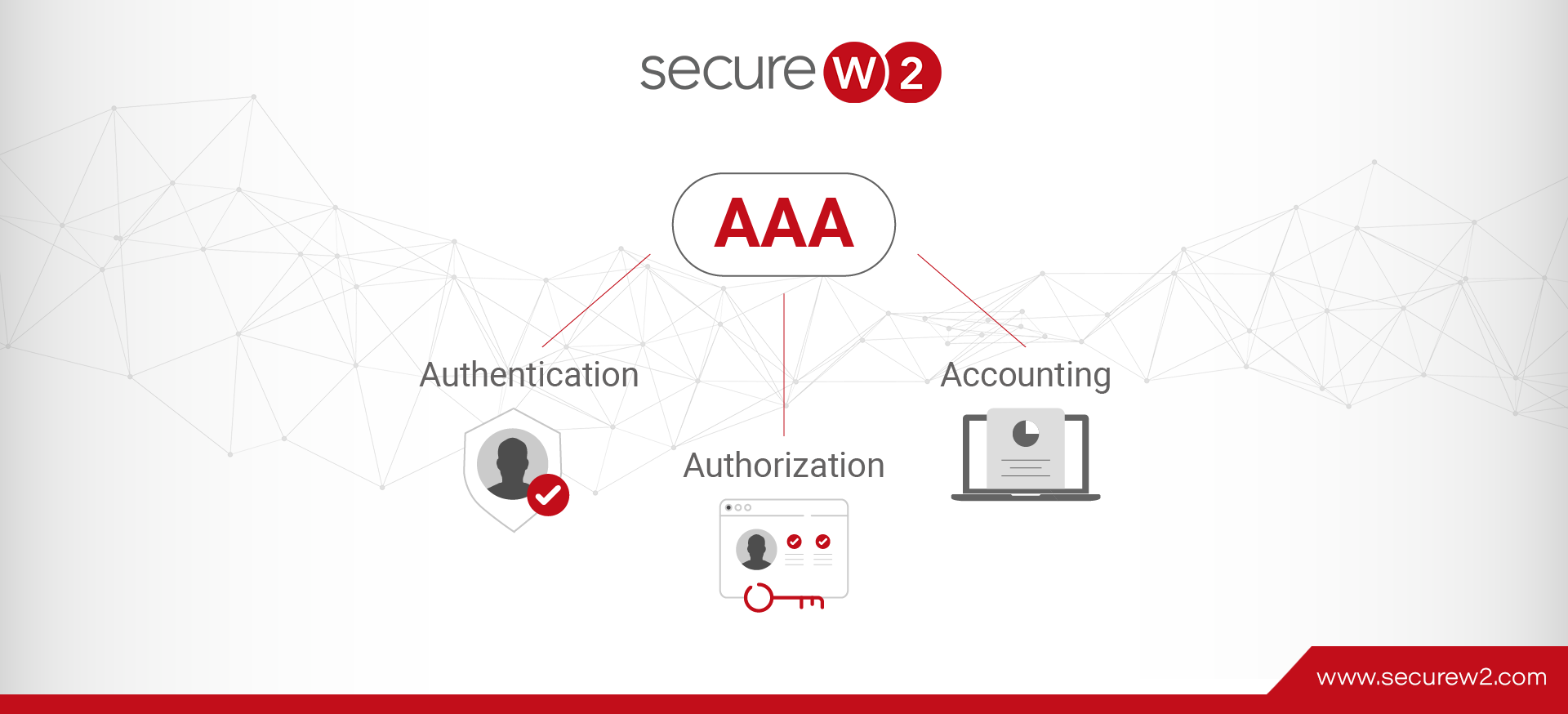
Authentication and Authorization. Visit systemdesign.us for System Design… | by PB | SystemDesign.us Blog | Medium



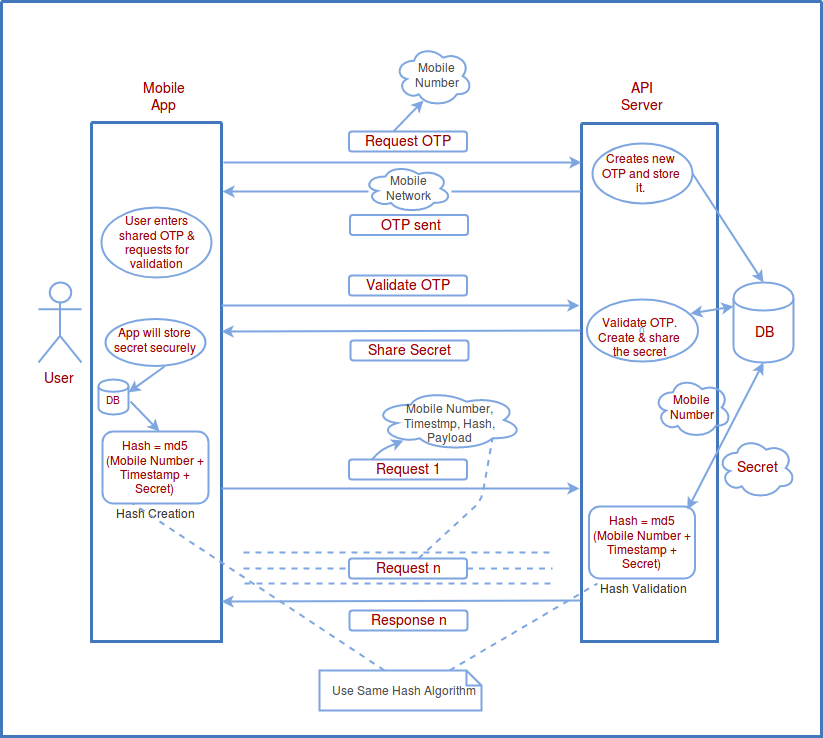





![13 User Authentication Platforms [Auth0, Firebase Alternatives] - Geekflare 13 User Authentication Platforms [Auth0, Firebase Alternatives] - Geekflare](https://geekflare.com/wp-content/uploads/2022/02/best-user-authentication-platforms.jpg)
.png)
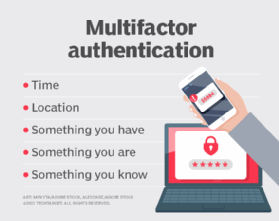
:max_bytes(150000):strip_icc()/twofactor-authentication-2fa.asp-final-5dc205d2a08b447abfb2e15eb131e28e.png)




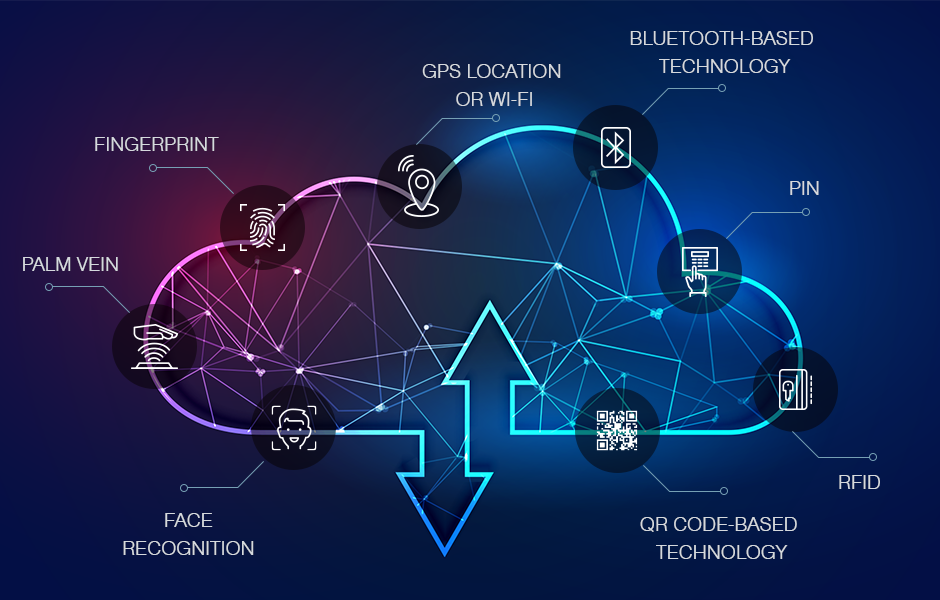
![What's the Best Authentication Method? Analysis [2024] What's the Best Authentication Method? Analysis [2024]](https://www.iproov.com/wp-content/uploads/2021/09/best-authentication-methods-v3-ai-1.png)